http://www.moneysavingexpert.com/news/protect/2016/03/stop-refunding-victims-of-online-fraud-police-chief-tells-banks
Mr Bernard Hogan-Howe recently stated that victims of online fraud should not be refunded. It worries me that a man of your power and position is incapable of understanding that being safe from fraud is not just a case of updating your software. The biggest factor in any hack is the human factor. The attacker is specifically hoping to take advantage of a weakness, whether he may pretend to a relative of the victim, or targets an employee of the financial institute to bypass any protection procedures in place.
It's common knowledge that in order for a claim of fraud to go through, and to protect the bank from malicious users, banks must do everything to protect their customers, in this case it could mean asking for additional confirmation with unfamiliar transactions. The user also has to show there was no negligence, e.g. pins were covered. The banks should be the people trying to prevent the fraud happening in the first place. If somehow the user has committed fraud, does that not point to flaws in the detection of these crimes? If the banks did their job, they would be able to stop these transactions going through in the first place.
People get smarter, they learn from their mistakes. The same thing happens with criminals. Credit card fraud isn't a small crime. It's big, there are gangs making millions. Do you really think that your systems would stop them? They've been milking your financial institution for ages, yet not one company has looked at resolving fraudulent transactions, or at least looking at how to reduce them.
I know certain online payment methods ask for additional verification when completing transactions, so why can't this be done for banks or online credit card payments?
It's not always the user that is at fault. No matter how good your software is, or how good you think you are with your personal information, these people have proven time after time that your virtual security does not mean anything. If they are able to find one weak link, especially a human one, then you never stood a chance in the first place.
It's not a case of just updating your systems, it's about educating people on safe practices.
Use HTTPS, make sure the green padlock is there. Don't use your information on sites which don't have a good reputation, you'll have no recourse. Look at additional safer methods to protect your card details, can you buy a gift card? Even in a case like this, what happens when the company themselves get breached, who protects the cardholders then?
"My broad point is that if you are continually rewarded for bad behavior you will probably continue to do it."
These people aren't doing this on purpose. Have you ever been a victim of fraud? Have you any idea how daunting it could be? Do you really think someone will be the victim of fraud twice through their own doing? They've been victims because it's your own system that has failed them in the first place. If you looked after your customers information, encrypted them accordingly, you wouldn't have breaches like the ones we've had that resulted in thousands of credit card details being leaked. If that information was encrypted, it wouldn't even be a problem right now. Your systems get abused on a daily basis by these criminals and you want to shift the blame on the user? You can only do so much to educate the user, you can implement policies that protect both parties but at the of the day, the weak point in this chain is not the user, it's the failure to detect these fraudulent transactions in the first place.
I agree that if I was told that if I didn't protect my PIN, if I'm hit by fraud then I am liable for charges.
The problem is, you're assuming everyone is breached because of their own fault. Almost every single case of credit card fraud has happened because the people committing the crime have been smarter, they've been duped into handing over CC details on what they believed was secure communication lines, or they were just unlucky and got affected like the victims of the Target breach.
As part of the police, your job is to provide the public with the tools so they can be more aware of these scams and learn to protect themselves better. The public look to you to provide them with the support they need, instead you tell them their pretty much on their own if they didn't know. It's not like these people are committing crimes when they get targeted, they've not been aware of what's been happening to them. Do you know how credit cards get harvested? Either through breaches of cardholders, ie online stores, or when cards have been intercepted, ie, skimming. Neither of these were the customers fault so would you put the blame on them?
You should be making your ATMs more secure so criminals can't install unauthorized devices and making mandatory regulations that anyone who holds certain information must be handling it securely. Failure to comply with those regulations and you get fined for endangering customers. The same way courier scams take advantage of the fact that a customer is not protected if he hands over his card and pin to anyone else, the fraudsters take advantage of weaknesses in your system. The courier scam victim would have to pay back all the losses, but why should they be held responsible if you allowed a stolen transaction to go through approval, despite the transaction appearing from a device that's not familiar, or from a different location. These people get away with it because people let them. They take advantage of gift shipping options as to avoid conflicts with billing & shipping addresses, that's not an issue with the people, it's an issue with the system processing the payment.
Credit card fraud happens because your own payment systems get abused and tricked. The same way Amazon protects me by asking me for my full credit card number, if I log in from another device or a different location, banks need to offer more protection, so just having a set of details doesn't mean the abuser is always going to get away with it.
Focus more on educating and preventing rather than shifting blame. It also helps if you look at the root cause of an issue rather than assuming you can update your systems and be safe, if that was the case, no one would be getting hacked.
Sunday 27 March 2016
Monday 19 November 2012
SudoCC.org
 | ||
| SudoCC.org home/login page. |
I came across this site being spammed on many forums, and I wanted to look into this further. What kind of criminal spams his illegal website on a public forum that is probably monitored by the respective authorities? Probably not a smart one so I wanted to see what I could dig up just from the website and free tools, usable by anyone.
 | ||
| IP Lookup |
Well the first thing I did was use a Firefox plugin called FlagFox. All I have to do is click the flag in the URL bar (which already shows the hosting country) and I get redirected to a site which shows a map, and the following details.
You can confirm these yourself by checking here:
http://geoip.flagfox.net/?ip=50.7.199.221&host=www.sudocc.org
So for starters, at least it's not hosted in the US....so he's safe...right?
So the next thing I did was look up the IP of the server hosting the content and were presented with the following information. So we can clearly see FDCservers.net is the host. We've also got the contact information for their abuse & support departments should we require them. Next step? Let's visit the FDCServers AUP (Acceptable Use Policy Website.)
Uh oh...FDC Servers do NOT support illegal activities. ( http://fdcservers.net/aup.php ) FDC servers are also hosted in the US, so that means we have a hacker / vendor who is selling credit card and financial data on a US hosted smart...either we have a honeypot, someone very desperate or an idiot.
http://whois.domaintools.com/sudocc.org
What else can we do? Let's check out the domain registrar. Finally, we're seeing SOME sense. He's enabled domain WHOIS privacy. Must be impossible to get busted from this right....
Well...let's go and ask Gossimer.com what they think;
http://www.gossimer.com/tos.html
Nope...Gossimer isn't having any of that either. So we have a vendor, who is selling the financial data, which is illegal and has a domain that is from a US based site which strictly prohibits the use of their services for such activities...and is hosted on a US based site.
Honeypot / It's a tarp!
Desperate individual who cannot afford off-shore hosting?
An idiot.
You decide.
If you're going to enter the online cyber-crime world....at least do it properly.
Labels:
credit card shop,
fdcservers,
gossimer,
sudocc,
Sudocc.org
Thursday 22 March 2012
[FIX] Couldn't Bind HTTPS Acceptor Socket

I recently got back into network analysis and thought I should refresh my skills with the most common tool, Cain & Abel. It's not the most user friendly but imho it's the most comprehensive. Has almost everything you could want in one nifty tool. However, I reached a snag when attempting to capture packets over a device that was on my network. This annoying error message isn't really descriptive nor does it offer much help. Thankfully, this post should clear it up for users like me who have had trouble with this message.
The message simply means that something is already using the HTTPS (443) port on your machine. Now there are two things you should do to fix this and ensure it stays that way. The first thing you need to do is disable HTTPS sniffing.
Open up C&A. Go to Configure -> Filters & Ports and untick the HTTPS box. Press Apply and then OK.
 The next thing to do is download something called TCPview. (Click Here) Open it up and this is what you're looking for.
The next thing to do is download something called TCPview. (Click Here) Open it up and this is what you're looking for.

Now it may not be Skype that's using the HTTPS port, it could be anything. Just click on the Local Port tab at the top to sort by name and scroll down till you find either HTTPS or 443. End the process and voila. HTTPS is no longer in use and your back on track.
The message simply means that something is already using the HTTPS (443) port on your machine. Now there are two things you should do to fix this and ensure it stays that way. The first thing you need to do is disable HTTPS sniffing.
Open up C&A. Go to Configure -> Filters & Ports and untick the HTTPS box. Press Apply and then OK.
 The next thing to do is download something called TCPview. (Click Here) Open it up and this is what you're looking for.
The next thing to do is download something called TCPview. (Click Here) Open it up and this is what you're looking for.
Now it may not be Skype that's using the HTTPS port, it could be anything. Just click on the Local Port tab at the top to sort by name and scroll down till you find either HTTPS or 443. End the process and voila. HTTPS is no longer in use and your back on track.
Thursday 28 October 2010
IJJI.com Hacked.
Update - it seems like IJJI.com has been hacked about 4 times now, each by different groups. As of this update it directs to DXT gaming (http://dxtgaming.com/) All I can say is iJJi is getting owned pretty hard, you would think that they would have some sort of protection for such a sophisticated gaming network but instead they've left themselves vulnerable to many attacks. Let's hope the sites DB or any personal information wasn't extracted. Just goes to show not every site is safe from attack.
Some are saying it was an ex-webmaster but nothing has been confirmed atm. Either way props to the group and hopefully this will be a lesson to Ijji to fix up their security.
Sunday 4 July 2010
YouTube Gets Exploited.
Updated #2 - I've heard reports that Tinkode came out with the 0day exploit. Props to him for an pretty awesome find. Many of you will recognize TinKode if you read his security blog or have seen him around at HF.
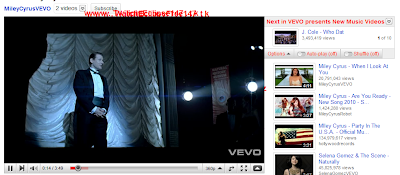
Updated: All comments have been hidden whilst YouTube fixes the situation. Maybe now would be the time for them to sanitize inputs?
YouTube was bombarded with spam today after a code was released which allowed HTML to be posted in comments. This was advanced on and led to customisable javascript alerts and full page "ads" as well as complete page redirects now. See images below and check out YouTube whilst it's still not been fixed.



Labels:
4th july youtube,
hack youtube,
javascript hack,
xch4ng3,
youtube hacked
Friday 11 June 2010
Taking Back Hacker.
I thought it was about time I wrote this up. This post is in response to Omniscient's post regarding Taking Back Hacker.
"I am sick of hearing how the term "hacker" means you're a criminal. I'd like to start a serious campaign to spread the message that hackers are people that are computer enthusiasts using computers in unorthodox and creative ways. Hackers are people that think outside the box. Hackers learn to manipulate code, hardware, and software.
I think the time has come to undo the damage the media has done to the good name of hackers by slurring the term on the airwaves and damaging reputations everywhere.
Any good website will give multiple meanings for the term hacker. It was originally not intended to be criminals that use computers to commit crime. But now this is the public perception and it hurts all of us. I don't see why I can't be a proud hacker and have to hide it amongst friends as if it's something shameful. "
This is my part in this campaign if you will. Firstly, I think the term hacking has been almost criminalised by the media. Nearly all of the time when hackers or any sort of hacking is mentioned in the media it is in a negative view. The rare times that it's shown in a good light, it's not very beneficial to the world, so most just dismiss it. This only shows one side of the story and shouldn't act as a reference to the whole idea of a hacker. Hacking can be viewed in different ways, but firstly we must understand that they're are different types of hackers.
- White Hat Hackers.
These are the good guys. White Hat hackers are the angels of the computing world. They are people who use unorthodox and uncommon ways of protecting computers. Whilst most do not dabble in any sort of blackhat activity, many are skilled in (and some are ex blackhats) and have vast knowledge of how blackhats operate and the techniques they use. They can then use this knowledge to come up with a defence of their own.
- Grey Hat Hackers.
Grey hat hackers are in the middle. They have knowledge of both black hat and white hat activities, however they can go either way. Some decide to protect themselves by using blackhat techniques against their attackers (eye for an eye mentality.) whilst others just choose to go either way whenever they feel like it. It really depends on the person.
- Black Hat Hackers.
Black hat hackers exist simply to cause damage or do anything to get their own way. They will not give a second thought about causing damage or breaking into a system for their own needs.
So as you can see, there are many aspects to hacking then you originally think. The aim of hacking is not always to cause damage, but instead it can be used for various thing - protection, to gain more knowledge and even for fun and creativity.
As we have advanced into a new age, a new generation must arise. This is no different in the hacking community. Over the past few years (and even from the start in some cases) a new generation of so called hackers has arisen. The hacking community refers to these as script kiddies. Script kiddies (or skiddies.) are people who use tools created by legitimate hackers without having any idea what they do. A good example of this was David Lennon who used Avalanche - a mail bomber to email bomb his employer, which crashed the email servers (source.) Script kiddies often have no understanding of how things work, sometimes even leeching other's work without credit. Then we move onto the hackers who think they are actually hackers because they use tools like RATs or hostbooters. I think I speak for the rest of the community when I say that they do not represent us as a whole. They have tarnished the name of hackers just because they can pay someone to set up a botnet for them and enter some simple commands.
If you've ever seen Hackers Wanted it sums up how I feel about this. The movie makes some good points, and some I agree with strongly. Society is based around conformity, you all answer to a higher authority - whether it be a boss, parent or even God. You all answer to someone. You all have some sort of job, go to school and conform in some sort of way. So when someone like a hacker breaks that conformity, society isn't going to accept it nicely. As long as someone who breaks that conformity exists, society will always have someone to blame - and why's that? Because they're different. You wouldn't blame them if they followed your way. However, what most people fail to realise is that if you don't dare to break the current boundaries, you can't ever expect to advance. Your just stuck inside your box, living the same way.
So the next time you decide to label a hacker, have a think. Some of them are the reason your living the way you are right now.
If you've ever seen Hackers Wanted it sums up how I feel about this. The movie makes some good points, and some I agree with strongly. Society is based around conformity, you all answer to a higher authority - whether it be a boss, parent or even God. You all answer to someone. You all have some sort of job, go to school and conform in some sort of way. So when someone like a hacker breaks that conformity, society isn't going to accept it nicely. As long as someone who breaks that conformity exists, society will always have someone to blame - and why's that? Because they're different. You wouldn't blame them if they followed your way. However, what most people fail to realise is that if you don't dare to break the current boundaries, you can't ever expect to advance. Your just stuck inside your box, living the same way.
So the next time you decide to label a hacker, have a think. Some of them are the reason your living the way you are right now.
Labels:
Hackers wanted,
Omniscient,
Taking Back Hacker,
xch4ng3
Thursday 15 October 2009
Bad Boys II - Vista Fix [Error During Babel Installation]
Below is just a back story. I felt in the typing mood so I thought why not. If you want the fix, just scroll down.
Recently I purchased a copy of Bad Boys II for the PC. I know. It's a shit game, but I had some fun memories of playing the promotional copy that was given out about 12 years ago that I decided to buy a full copy. At first I tried to obtain it via "sources" but every time I attempted to play, I was greeted with the message "Error during babel installation". I tried everything I knew at that time, various registry edits, checking for conflicts, reinstalling, searching Google and even the method I'm about to show you now. For some weird reason it works now, but didn't seem to work back then. Anyway, I ended giving up on the game, coming to the conclusion that it probably wasn't work because it was a copied game.
I then came across the game on eBay for about £1.99. I decided to buy it, hoping that it would work...and if it didn't, oh well. Not much of a loss. I ordered the game and installed it. To my annoyance, it failed to work. I decided to contact the supplier of the game and I was told
"The issue is sometimes linked to the Graphics Controller Chipset. We would recommend that you check with the PC Manufacturers website and see if there is an updated driver for your Graphics Card. If there is then download and install the update. Also ensure you have the following resolution settings 1024 x 768 32 bit colour.
To change your screen resolution / colour settings Open Display in Control Panel.
Windows XP = To open Display, click Start, click Control Panel, and then click Display.
Recently I purchased a copy of Bad Boys II for the PC. I know. It's a shit game, but I had some fun memories of playing the promotional copy that was given out about 12 years ago that I decided to buy a full copy. At first I tried to obtain it via "sources" but every time I attempted to play, I was greeted with the message "Error during babel installation". I tried everything I knew at that time, various registry edits, checking for conflicts, reinstalling, searching Google and even the method I'm about to show you now. For some weird reason it works now, but didn't seem to work back then. Anyway, I ended giving up on the game, coming to the conclusion that it probably wasn't work because it was a copied game.
I then came across the game on eBay for about £1.99. I decided to buy it, hoping that it would work...and if it didn't, oh well. Not much of a loss. I ordered the game and installed it. To my annoyance, it failed to work. I decided to contact the supplier of the game and I was told
"The issue is sometimes linked to the Graphics Controller Chipset. We would recommend that you check with the PC Manufacturers website and see if there is an updated driver for your Graphics Card. If there is then download and install the update. Also ensure you have the following resolution settings 1024 x 768 32 bit colour.
To change your screen resolution / colour settings Open Display in Control Panel.
Windows XP = To open Display, click Start, click Control Panel, and then click Display.
On the Settings tab, under Display Properties, drag the screen area slider to the required setting, and then click Apply.
A default setting of 1024 x 768 is a standard option to set this to. Also ensure that your colour quality is set to either highest 32bit or true colour 32 bit. When prompted to apply the settings, click OK. Your screen will turn black for a moment. Once your screen resolution changes, you have 15 seconds to confirm the change.
Click Yes to confirm the change; click No or do nothing to revert to your previous setting.
If this does not resolve the issue then the issue will be a compatibility problem with the Graphics Card and you will possibly not be able to resolve the problem.
Bad Boys II requires a 3d video card with at least 32Mb of memory that can display 16bit colour or better. The primary video card in your machine MUST have at least 32Mb of memory for Bad Boys II to run, the memory of any additional accelerator cards will not necessarily be taken into account. If your video card has insufficient memory the game will not run correctly, or at all."
Bad Boys II requires a 3d video card with at least 32Mb of memory that can display 16bit colour or better. The primary video card in your machine MUST have at least 32Mb of memory for Bad Boys II to run, the memory of any additional accelerator cards will not necessarily be taken into account. If your video card has insufficient memory the game will not run correctly, or at all."
I tried all the above, and once again to my annoyance...no luck. After another good hour messing around with settings and tweaking I finally came to the solution. It's simply that Bad Boys II wasn't designed to be run on a machine running anything higher than Windows XP. The solution? Compatability Mode.
======
The Fix
======
The long awaited solution. Thankfully it doesn't involve anything too technical and everyone who has a simple understanding of computers will be able to perform the fix.
First, make sure the game is installed correctly. Once installed, Right Click on the launcher icon and click on Properties.
Switch to the compatibility tab and make sure your settings match mine.
Fixed.
Labels:
babel,
bad boys ii,
during,
error,
fix,
installation,
pc
Subscribe to:
Posts (Atom)